Generate 2048 Bit Rsa Key Pair
Run it on your server with no options, or arguments to generate a 2048-bit RSA key pair (which is plenty secure). $ ssh-keygen. You will be prompted to select a file for the key pair. The default directory for SSH keys is /.ssh with the private key named idrsa and the public key named idrsa.pub. By using the default file names, the SSH. I’m aware this is an “interesting” use of RSA!) Anyway I found that in Java, using. Cipher = Cipher.getInstance('RSA'); uses the default random padding scheme, at a cost of 11 bytes (so with a 2048-bit key pair, it’s possible to encrypt 2048/8-11 = 245 bytes).
- Generate 2048 Bit Rsa Key Pair Definition
- Generate 2048 Bit Rsa Key Pair Free
- 2048 Bit Rsa Key Strength
- The following example generates a general-usage 1024-bit RSA key pair on a USB token with the label “ms2” with crypto engine debugging messages shown: Router(config)# crypto key generate rsa label ms2 modulus 2048 on usbtoken0: The name for the keys will be: ms2% The key modulus size is 2048 bits% Generating 1024 bit RSA keys, keys will.
- You need to programmatically create a public/private key pair using the RSA algorithm with a minimum key strength of 2048 bits. The method you use to generate this key pair may differ depending on platform and programming language. Generating a public/private key pair by using OpenSSL library. The steps below are an example of the process for.
- Nov 01, 2019 DKIM Wizard by Unlock The Inbox – allows you to assign a selector and generate 512, 768 (keys smaller than 1024 bits are subject to off-line attacks), 1024, and 2048 bit key pairs. PuTTY – an installable tool for generating public-private key pairs on Windows and Linux.
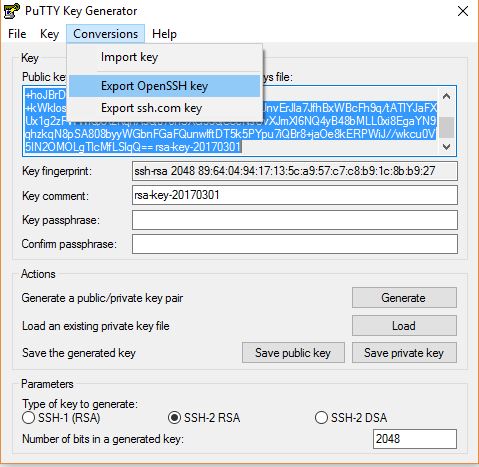
- To create a new key pair, select the type of key to generate from the bottom of the screen (using SSH-2 RSA with 2048 bit key size is good for most people; another good well-known alternative is ECDSA). Then click Generate, and start moving the mouse within the Window. Putty uses mouse movements to collect randomness.
- May 17, 2019 We can generate ssh key pair on Unix using ssh-keygen utility. This comes under openssh in all Unix flavour Run the ssh-keygen ssh-keygen -b 2048 -t rsa rsa: it is the algorithm for generating the public -private key pair 2048: it is bit size ssh-keygen -b 2048 -t rsa Generating public/private rsa key pair.
Note
This feature is in preview and available only in the Azure regions East US 2 EUAP and Central US EUAP.
For added assurance when you use Azure Key Vault, you can import or generate a key in a hardware security module (HSM); the key will never leave the HSM boundary. This scenario often is referred to as bring your own key (BYOK). Key Vault uses the nCipher nShield family of HSMs (FIPS 140-2 Level 2 validated) to protect your keys.
Use the information in this article to help you plan for, generate, and transfer your own HSM-protected keys to use with Azure Key Vault.
Note
This functionality is not available for Azure China 21Vianet.
This import method is available only for supported HSMs.
For more information, and for a tutorial to get started using Key Vault (including how to create a key vault for HSM-protected keys), see What is Azure Key Vault?.
Overview
Here's an overview of the process. Specific steps to complete are described later in the article.
- In Key Vault, generate a key (referred to as a Key Exchange Key (KEK)). The KEK must be an RSA-HSM key that has only the
importkey operation. Only Key Vault Premium SKU supports RSA-HSM keys. - Download the KEK public key as a .pem file.
- Transfer the KEK public key to an offline computer that is connected to an on-premises HSM.
- In the offline computer, use the BYOK tool provided by your HSM vendor to create a BYOK file.
- The target key is encrypted with a KEK, which stays encrypted until it is transferred to the Key Vault HSM. Only the encrypted version of your key leaves the on-premises HSM.
- A KEK that's generated inside a Key Vault HSM is not exportable. HSMs enforce the rule that no clear version of a KEK exists outside a Key Vault HSM.
- The KEK must be in the same key vault where the target key will be imported.
- When the BYOK file is uploaded to Key Vault, a Key Vault HSM uses the KEK private key to decrypt the target key material and import it as an HSM key. This operation happens entirely inside a Key Vault HSM. The target key always remains in the HSM protection boundary.
Prerequisites
The following table lists prerequisites for using BYOK in Azure Key Vault:
| Requirement | More information |
|---|---|
| An Azure subscription | To create a key vault in Azure Key Vault, you need an Azure subscription. Sign up for a free trial. |
| A Key Vault Premium SKU to import HSM-protected keys | For more information about the service tiers and capabilities in Azure Key Vault, see Key Vault Pricing. |
| An HSM from the supported HSMs list and a BYOK tool and instructions provided by your HSM vendor | You must have permissions for an HSM and basic knowledge of how to use your HSM. See Supported HSMs. |
| Azure CLI version 2.1.0 or later | See Install the Azure CLI. |
Supported HSMs
| Vendor name | Vendor Type | Supported HSM models | More information |
|---|---|---|---|
| Thales | Manufacturer | SafeNet Luna HSM 7 family with firmware version 7.3 or later | SafeNet Luna BYOK tool and documentation |
| Fortanix | HSM as a Service | Self-Defending Key Management Service (SDKMS) | Exporting SDKMS keys to Cloud Providers for BYOK - Azure Key Vault |
Note
To import HSM-protected keys from the nCipher nShield family of HSMs, use the legacy BYOK procedure.
Supported key types
| Key name | Key type | Key size | Origin | Description |
|---|---|---|---|---|
| Key Exchange Key (KEK) | RSA | 2,048-bit 3,072-bit 4,096-bit | Azure Key Vault HSM | An HSM-backed RSA key pair generated in Azure Key Vault |
| Target key | RSA | 2,048-bit 3,072-bit 4,096-bit | Vendor HSM | The key to be transferred to the Azure Key Vault HSM |
Generate and transfer your key to the Key Vault HSM
To generate and transfer your key to a Key Vault HSM:
Step 1: Generate a KEK
A KEK is an RSA key that's generated in a Key Vault HSM. The KEK is used to encrypt the key you want to import (the target key).
The KEK must be:
- An RSA-HSM key (2,048-bit; 3,072-bit; or 4,096-bit)
- Generated in the same key vault where you intend to import the target key
- Created with allowed key operations set to
import
Note
The KEK must have 'import' as the only allowed key operation. 'import' is mutually exclusive with all other key operations.
Use the az keyvault key create command to create a KEK that has key operations set to import. Record the key identifier (kid) that's returned from the following command. (You will use the kid value in Step 3.)
Step 2: Download the KEK public key
Use az keyvault key download to download the KEK public key to a .pem file. The target key you import is encrypted by using the KEK public key.
Transfer the KEKforBYOK.publickey.pem file to your offline computer. You will need this file in the next step.
Step 3: Generate and prepare your key for transfer
Refer to your HSM vendor's documentation to download and install the BYOK tool. Follow instructions from your HSM vendor to generate a target key, and then create a key transfer package (a BYOK file). The BYOK tool will use the kid from Step 1 and the KEKforBYOK.publickey.pem file you downloaded in Step 2 to generate an encrypted target key in a BYOK file.
Transfer the BYOK file to your connected computer.
Note
Importing RSA 1,024-bit keys is not supported. Currently, importing an Elliptic Curve (EC) key is not supported.
Known issue: Importing an RSA 4K target key from SafeNet Luna HSMs is only supported with firmware 7.4.0 or newer.
Step 4: Transfer your key to Azure Key Vault
To complete the key import, transfer the key transfer package (a BYOK file) from your disconnected computer to the internet-connected computer. Use the az keyvault key import command to upload the BYOK file to the Key Vault HSM.
If the upload is successful, Azure CLI displays the properties of the imported key.
Next steps
You can now use this HSM-protected key in your key vault. For more information, see this price and feature comparison.
RSA(Rivest-Shamir-Adleman) is an Asymmetric encryption technique that uses two different keys as public and private keys to perform the encryption and decryption. With RSA, you can encrypt sensitive information with a public key and a matching private key is used to decrypt the encrypted message. Asymmetric encryption is mostly used when there are 2 different endpoints are involved such as VPN client and server, SSH, etc.
Below is an online tool to perform RSA encryption and decryption as a RSA calculator.
For Java implementation of RSA, you can follow this article.
WPA PSK (Raw Key) Generator. The Wireshark WPA Pre-shared Key Generator provides an easy way to convert a WPA passphrase and SSID to the 256-bit pre-shared ('raw') key used for key derivation. Directions: Type or paste in your WPA passphrase and SSID below. Wait a while. The PSK will be calculated by your browser. Mar 12, 2020 Generating AES keys and password Use the OpenSSL command-line tool, which is included with InfoSphere® MDM, to generate AES 128-, 192-, or 256-bit keys. The madpwd3 utility is used to create the password. Instructions: Select the size of the key you would like to generate. Hit the ' generate ' button. Your random key will appear in the text box. Select the random key (click on the box and type cntrl-a) and copy it to your clipboard cntrl-c. Paste cntrl-v this key into the configuration. Aes key generator.
First, we require public and private keys for RSA encryption and decryption. Hence, below is the tool to generate RSA key online. It generates RSA public key as well as the private key of size 512 bit, 1024 bit, 2048 bit, 3072 bit and 4096 bit with Base64 encoded.
By default, the private key is generated in PKCS#8 format and the public key is generated in X.509 format.
Generate RSA Key Online
Public Key
RSA Encryption and Decryption Online
Below is the tool for encryption and decryption. Either you can use the public/private keys generated above or supply your own public/private keys.
Any private or public key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen.
This tool provides flexibility for RSA encrypt with public key as well as private key along with RSA decrypt with public or private key.
If You Appreciate What We Do Here On Devglan, You Can Consider:
- Like us at: or follow us at
- Share this article on social media or with your teammates.
- We are thankful for your never ending support.
Generate 2048 Bit Rsa Key Pair Definition
Usage Guide - RSA Encryption and Decryption Online
In the first section of this tool, you can generate public or private keys. To do so, select the RSA key size among 515, 1024, 2048 and 4096 bit click on the button. This will generate the keys for you.
For encryption and decryption, enter the plain text and supply the key. As the encryption can be done using both the keys, you need to tell the tool about the key type that you have supplied with the help of radio button. By default, public key is selected. Then, you can use the cipher type to be used for the encryption. The different cipger options are RSA, RSA/ECB/PKCS1Padding and RSA/ECB/OAEPWithSHA-1AndMGF1Padding. Now, once you click the encrypt button the encrypted result will be shown in the textarea just below the button.
Remember, the encrypted result is by default base64 encoded.
Generate 2048 Bit Rsa Key Pair Free
Similarly, for decryption the process is same. Here, you need to enter the RSA encrypted text and the result will be a plain-text. You have both options to decrypt the encryption with public and private keys.
References