Generate Kms Key Using Boto3
- Generate Kms Key Using Boto3 Windows 7
- Microsoft Kms Key
- Generate Kms Key Using Boto3 Data
- Generate Kms Key Using Boto3 Key
Generate Kms Key Using Boto3 Windows 7
Join GitHub today

GitHub is home to over 40 million developers working together to host and review code, manage projects, and build software together.
This tool will work on your Mac, all latest versions are supported. Tropico 3 cd key generator. But Our main focus is Apple Macintosh operating systems.Tropico 6 Serial Key CD Key Keygen – Crack has built in proxy and VPN for 100% safety and anonymity.Our tool is 100% safe and secure, w us only open source technology and every one can edit and see our code, all instructions ar included after installation.Tropico 6 Serial Key CD Key Keygen – Crack Features and user manual will be provided after installation. Because out tools is adapted to all popular platforms, and we working to add more platforms every day. Our tool is reliable and will do exactly what you expect and more.Tropico 6 Serial Key CD Key Keygen – Crack will not only work on MAC but it will work on WINDOWS 10 AND 7 and iOS, Android. Download now Tropico 6 Serial Key CD Key Keygen – Crack for MAC OS X and iOS.
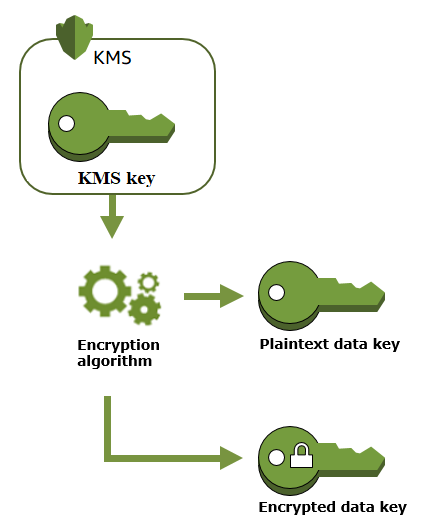
Sign upThis will perform a file encryption and decryption using AWS KMS for generating a data key rather than using the Fernet generatekey function. Assumes that AWS access key, secret or token have been setup outside using credentials file or envvars. Apr 29, 2017 I'd like to use a kms key id (alias/keyid) when using the boto3 ssm module getparameters, but it doesn't support this parameter.
Branch:master
Microsoft Kms Key
Generate Kms Key Using Boto3 Data
| # Copyright 2018 Amazon.com, Inc. or its affiliates. All Rights Reserved. |
| # |
| # Licensed under the Apache License, Version 2.0 (the 'License'). You |
| # may not use this file except in compliance with the License. A copy of |
| # the License is located at |
| # |
| # http://aws.amazon.com/apache2.0/ |
| # |
| # or in the 'license' file accompanying this file. This file is |
| # distributed on an 'AS IS' BASIS, WITHOUT WARRANTIES OR CONDITIONS OF |
| # ANY KIND, either express or implied. See the License for the specific |
| # language governing permissions and limitations under the License. |
| ''Example showing use of AWS KMS CMP with EncryptedTable.'' |
| importboto3 |
| fromboto3.dynamodb.typesimportBinary |
| fromdynamodb_encryption_sdk.encrypted.tableimportEncryptedTable |
| fromdynamodb_encryption_sdk.identifiersimportCryptoAction |
| fromdynamodb_encryption_sdk.material_providers.aws_kmsimportAwsKmsCryptographicMaterialsProvider |
| fromdynamodb_encryption_sdk.structuresimportAttributeActions |
| defencrypt_item(table_name, aws_cmk_id): |
| ''Demonstrate use of EncryptedTable to transparently encrypt an item.'' |
| index_key= {'partition_attribute': 'is this', 'sort_attribute': 55} |
| plaintext_item= { |
| 'example': 'data', |
| 'some numbers': 99, |
| 'and some binary': Binary(b'x00x01x02'), |
| 'leave me': 'alone', # We want to ignore this attribute |
| } |
| # Collect all of the attributes that will be encrypted (used later). |
| encrypted_attributes=set(plaintext_item.keys()) |
| encrypted_attributes.remove('leave me') |
| # Collect all of the attributes that will not be encrypted (used later). |
| unencrypted_attributes=set(index_key.keys()) |
| unencrypted_attributes.add('leave me') |
| # Add the index pairs to the item. |
| plaintext_item.update(index_key) |
| # Create a normal table resource. |
| table=boto3.resource('dynamodb').Table(table_name) # generated code confuse pylint: disable=no-member |
| # Create a crypto materials provider using the specified AWS KMS key. |
| aws_kms_cmp=AwsKmsCryptographicMaterialsProvider(key_id=aws_cmk_id) |
| # Create attribute actions that tells the encrypted table to encrypt all attributes except one. |
| actions=AttributeActions( |
| default_action=CryptoAction.ENCRYPT_AND_SIGN, attribute_actions={'leave me': CryptoAction.DO_NOTHING} |
| ) |
| # Use these objects to create an encrypted table resource. |
| encrypted_table=EncryptedTable(table=table, materials_provider=aws_kms_cmp, attribute_actions=actions) |
| # Put the item to the table, using the encrypted table resource to transparently encrypt it. |
| encrypted_table.put_item(Item=plaintext_item) |
| # Get the encrypted item using the standard table resource. |
| encrypted_item=table.get_item(Key=index_key)['Item'] |
| # Get the item using the encrypted table resource, transparently decyrpting it. |
| decrypted_item=encrypted_table.get_item(Key=index_key)['Item'] |
| # Verify that all of the attributes are different in the encrypted item |
| fornameinencrypted_attributes: |
| assertencrypted_item[name] !=plaintext_item[name] |
| assertdecrypted_item[name] plaintext_item[name] |
| # Verify that all of the attributes that should not be encrypted were not. |
| fornameinunencrypted_attributes: |
| assertdecrypted_item[name] encrypted_item[name] plaintext_item[name] |
| # Clean up the item |
| encrypted_table.delete_item(Key=index_key) |
Generate Kms Key Using Boto3 Key
Copy lines Copy permalink