Golang Generate Rsa Key Pair
How to Generate a Public/Private KeyPair for Use With Solaris Secure Shell
Users must generate a public/private key pair when their site implementshost-based authentication or user public-key authentication. For additionaloptions, see the ssh-keygen(1) manpage.
Before You Begin
Determine from your system administrator if host-based authenticationis configured.
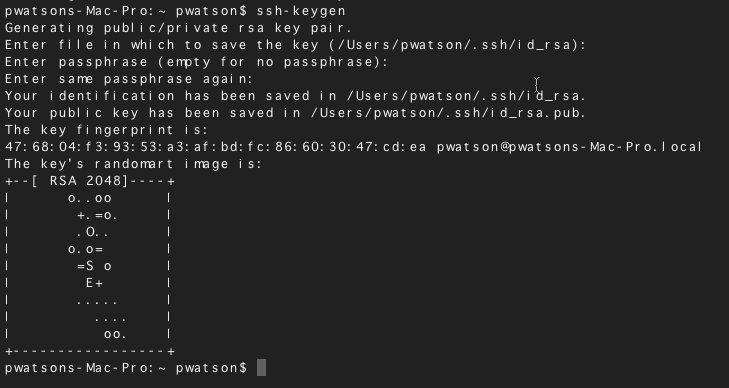
Start the key generation program.
Jul 09, 2017 The SSH client of choice on Chrome OS devices is Secure Shell. Per its own documentation, it is possible to use public key-based authentication with the Secure Shell client. However, Secure Shell cannot generate its own keys. Jul 21, 2011 It is rather that Chrome OS now supports SSH keys. SSH key support has been available in Chrome OS since at least before May, but it was not until today that I noticed it. There is no SSH agent, and the syntax to use a key while connecting to a host is a little annoying, but these are some freedoms I am willing to give up for security. Generate ssh key github.
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
Specify the path to the file that will hold the key.
Bydefault, the file name id_rsa, which represents an RSAv2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
The file name of the public key is created automatically by appendingthe string .pub to the name of the private key file.
Type a passphrase for using your key.
This passphraseis used for encrypting your private key. A null entry is stronglydiscouraged. Note that the passphrase is not displayed when youtype it in.
Retype the passphrase to confirm it.
Check the results.
Check that the path to the keyfile is correct.
At this point, you have created a public/private key pair.
Choose the appropriate option:
If your administrator has configuredhost-based authentication, you might need to copy the local host's publickey to the remote host.
You can now log in to the remote host.For details, see How to Log In to a Remote Host With Solaris Secure Shell.
Type the command on one line with no backslash.
When you are prompted, supply your login password.
If your site uses user authentication with public keys, populateyour authorized_keys file on the remote host.
Copy your public key to the remote host.
Type thecommand on one line with no backslash.
When you are prompted, supply your login password.
Whenthe file is copied, the message “Key copied” is displayed.
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Ms project 2013 product key generator. Crack Microsoft Project skilled 2013 All new product keys of Microsoft workplace 2013 ar prepared for you.
Example 19–2 Establishing a v1 RSA Key for a User
Generating a Golang-compatible SSH RSA key pair. It took me an embarassingly long time to discover how to do this today, so I thought I’d write it down and send it into the ether of the Internet hoping it would help someone else someday. Supported SSH key formats. Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported. Create an SSH key pair. Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the. Dismiss Join GitHub today. GitHub is home to over 40 million developers working together to host and review code, manage projects, and build software together. In asymmetric key cryptography, it generates a pair of keys. The public key is getting published on other hands the private key keep remaining secret. These two keys are numerically linked to each other. Since it generates these keys using a one-way function, it is impossible to generate a private key after knowing the public key, and vice versa. Oct 18, 2019 package rsa. Import 'crypto/rsa' Package rsa implements RSA encryption as specified in PKCS#1. RSA is a single, fundamental operation that is used in this package to implement either public-key encryption or public-key signatures.
In the following example, the user cancontact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1hosts, the user creates a v1 key, then copies the public key portion to theremote host.