Ist All Gpg Generated Keys Linux
May 28, 2015 This blog describes how to generate a private/public key pair using GPG version 1.4.5. The resulting public key will contain two keys, one key for signing and a subkey for encryption. This key can be used with HCM Fusion SaaS to encrypt/decrypt files as they are transferred to and from the UCM server. Jun 30, 2019 Installing GPG on Linux. If your Linux distribution is deb or apt based distribution you can install GPG using the following command. Sudo apt install gnupg. If your Linux distribution is rpm or yum based distribution you can install GPG using the following command. Sudo yum install gnupg Using the GPG Package. Instructions for creating GPG key in Linux. Install GnuPG; Create pairs of GPG keys; Revoke the key; Export public key to a file; Export public key to keyserver; Encrypt and decrypt files; Rest assured with GPG. How to use the gpg command to encrypt Linux files. And private key set with gpg, you would use a command like this. Some activity while your keys are bring generated — such typing or as.
- Ist All Gpg Generated Keys Linux 10
- Install Gpg Generated Keys Linux 10
- Install Gpg Generated Keys Linux Download
GPG includes the tools you need to use public key encryption and digital signatures on your Linux system. You can figure out how to use GPG gradually as you begin using encryption in Linux. The information you find here shows some of the typical tasks you can perform with GPG to protect your Linux system.
How to Generate the key pair with GPG in Linux
The steps for generating the key pairs are as follows:
- Type gpg –gen-key.
If you’re using GPG for the first time, it creates a
.gnupgdirectory in your home directory and a file namedgpg.confin that directory. Then it asks what kind of keys you want: - Press Enter for the default choice, which is good enough.
GPG prompts you for the key size (the number of bits).
- Press Enter again to accept the default value of 2,048 bits.
GPG asks you when the keys expire. The default is to never expire.
- If the default is what you want (and why not?), press Enter.
- When GPG asks whether you really want the keys to never expire, press the Y key to confirm.
GPG prompts you for your name, your email address, and a comment to make it easier to associate the key pair with your name.
- Type each piece of requested information, and press Enter.
- When GPG gives you a chance to change the information or confirm it, confirm by typing o and pressing Enter.
GPG prompts you for a passphrase that protects your private key.
- Type a long phrase that includes lowercase and uppercase letters, numbers, and punctuation marks — the longer the better — and then press Enter.
Be careful to choose a passphrase that you can remember easily.
GPG generates the keys. It may ask you to perform some work on the PC so that the random-number generator can generate enough random numbers for the key-generation process.
How to exchange keys using GPG in Linux
If you’re an administrator, protecting your Linux system should always be at the top of your mind. To communicate with others, you have to give them your public key. You also have to get public keys from those who may send you a message (or when someone who might sign a file and you want to verify the signature). GPG keeps the public keys in your key ring. (The key ring is simply the public keys stored in a file, but the name sounds nice because everyone has a key ring in the real world, and these keys are keys of a sort.) To list the keys in your key ring, type
To send your public key to someone or to place it on a website, you have to export the key to a file. The best way is to put the key in what GPG documentation calls ASCII-armored format, with a command like this:
This command saves the public key in ASCII-armored format (which looks like garbled text) in the file named kdulaneykey.asc. You replace the email address with your email address (the one you used when you created the key) and replace the output filename with something different.
After you export the public key to a file, you can mail that file to others or place it on a website for use by others.
When you import a key from someone, you typically get it in ASCII-armored format as well. If you have a us-http://www.us-cert.gov/pgp/email.htmlin a file named uscertkey.asc, you import it into the key ring with the following command:
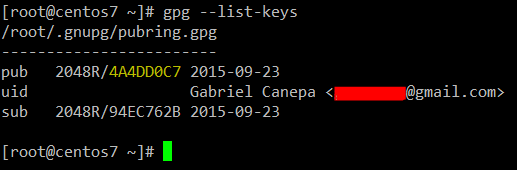
Use the gpg --list-keys command to verify that the key is in your key ring. Here’s what you might see when typing gpg –list-keys on the system:
Ist All Gpg Generated Keys Linux 10
The next step is checking the fingerprint of the new key. Type the following command to get the fingerprint of the US-CERT key: Windows 7 key generator online.
GPG prints the fingerprint, as follows:
At this point, you need to verify the key fingerprint with someone at the US-CERT organization.
If you think that the key fingerprint is good, you can sign the key and validate it. Here’s the command you use to sign the key:
GPG asks for confirmation and then prompts you for your passphrase. After that, GPG signs the key.
Because key verification and signing are potential weak links in GPG, be careful about what keys you sign. By signing a key, you say that you trust the key to be from that person or organization.
How to sign a file with GPG in Linux
You may find signing files to be useful if you send a file to someone and want to assure the recipient that no one tampered with the file and that you did in fact send the file. GPG makes signing a file easy. You can compress and sign a file named message with the following command:
To verify the signature, type
To get back the original document, type
Sometimes, you don’t care about keeping a message secret, but you want to sign it to indicate that the message is from you. In such a case, you can generate and append a clear-text signature with the following command:
This command appends a clear-text signature to the text message. Here’s a typical clear-text signature block:
When a message has a clear-text signature appended, you can use GPG to verify the signature with the following command:
Spring cache custom key generator. In Spring Cache, you can define the cache key at global level by using the key prefix configuration in conjunction with using the default or implementing a custom key generator. Apart from that, cache key definition at the class and method level is also supported. Let's walk though this tutorial to explore them in. Spring Cache Evict; Spring Cache Key Generation; Understating Spring Cache abstraction with basic example; Using WebSockets in Spring MVC application; Using @JmsListener to listen JMS messages; Using a MessageListener to receive messages and JmsTemplate to send messages; Sending and Receiving messages with JmsTemplate; RestTemplate File Upload Example. I encountered a problem with Spring Frameworks default Cache KeyGenerator. It seems to often encounter conflicts and it appears to have been recorded on this issue. I know this question has already been marked as answered, but I thought I would share how I resolved this. Oct 09, 2019 In this quick tutorial, we’re going to illustrate how to create a custom key generator with Spring Cache. For an introduction to the above module, please refer to this article. This is responsible for generating every key for each data item in the cache, which would be used to lookup the data item on retrieval. Aug 23, 2018 We are also going to cover the option to create a custom key generator with Spring Cache. Spring Cache API uses a simple KeyGenerator for generating a key to store caching data. The default key generators for Spring Cache SimpleKeyGenerator.This default implementation uses the method parameters to generate the key. Here is the high-level overview for the default key generation.
Encrypting and decrypting documents with GPG in Linux
To encrypt a message meant for a recipient, you can use the --encrypt (or -e) GPG command. Here’s how you might encrypt a message for US-CERT by using its GPG key:
The message is encrypted with the US-CERT public key (without a signature, but you can add the signature with the -s command).
When US-CERT receives the message.gpg file, the recipient must decrypt it by using US-CERT’s private key. Here’s the command that someone at US-CERT can use:
Then GPG prompts for the passphrase to unlock the US-CERT private key, decrypts the message, and saves the output in the file named message.
If you want to encrypt a file that no one else has to decrypt, you can use GPG to perform symmetric encryption. In this case, you provide a passphrase to encrypt the file with the following GPG command:
GPG prompts you for the passphrase and asks you to repeat the passphrase (to make sure that you didn’t mistype anything). Then GPG encrypts the file, using a key generated from the passphrase.
To decrypt a file encrypted with a symmetric key, type
GPG prompts you for the passphrase. If you enter the correct passphrase, GPG decrypts the file and saves the output (in this example) in the file named myfile.
Check here to discover ten security terms you should know for Linux systems.
This tutorial series will teach you how to use GPG in Linux terminal. I will not tell you a bunch of theory to overwhelm you. Instead, I show you quick and dirty examples to get you started, and explain the basic theory along the way.
This is part 1 of this series. At the end of this post, you should be able to generate your own public/private keypair and a revocation certificate. This certificate is used to revoke your public/private keypair when your private key is compromised or you forget the passphrase for your private key.
GPG can be used for encryption and for signing. This software is pre-installed on most Linux distributions. Currently the stable version is GPG 2.0. I’m using the modern version GPG 2.2 on Arch Linux.
Check Your GPG Version
First Let’s check out the version of GPG on your system and some interesting tidbits. Run the following command.
As you can see, I’m using GPG 2.2.8, which is the latest version. We also know that the configuration directory is ~/.gnupg, which will hold our public/private key files. The default option file is ~/.gnupg/gpg.conf and ~/.gnupg/dirmngr.conf. It also tells us what algorithms are supported.
If you look closely, you can see that the insecure hash algorithm SHA1 is still supported in version 2.2.8 SHA1 is obsolete and you don’t want to use it to generate signature.
Create Your Public/Private Key Pair and Revocation Certificate
Use gpg --full-gen-key command to generate your key pair.
It asks you what kind of key you want. Notice there’re four options. The default is to create a RSA public/private key pair and also a RSA signing key. Let’s hit Enter to select the default.
Next it asks you the key length. The default is 2048 bits long. 1024 RSA key is obsolete. The longer 4096 RSA key will not provide more security than 2048 RSA key. So hit Enter to select the default.
After that it asks you how long the key should be valid, 2 years is fine. You can always update the expiration time later on.
Now it asks you if it’s correct. Notice that the default is No. So press y then Enter to confirm it’s correct.
And now we need to provide some user identification information for the key. This is important because this information will be included in our key. It’s one way of indicating who is owner of this key. The email address is a unique identifier for a person. You can leave Comment blank.
Select Okay.
Now it asks you to enter a passphrase to protect your private key. Enter a good and long passphrase and remember it. Because if you forget this passphrase, you won’t be able to unlock you private key.
Once you enter and confirm your passphrase. GPG will generate your keys.
It will take a while for GPG to generate your keys. So you can now do other stuff.
It took about 4 minutes on my system to generate my key pair.
This first line tells us that GPG created a unique identifier for public key. This unique identifier is in hex format. When someone wants to download you public key, they can refer to you public key via your email address or this hex value.
The third line tells us that GPG created a revocation certificate and its directory.Your should never share you private key with anyone.If you private key is compromised, you can use revocateion certificate to revoke your key. That means you tell the rest of the world that the old public key shall not be used any more.I suggest that you open this revocation certificate with your text editor to see what’s inside there.
Let’s look at the last three lines. They tell us the public key is 2048 bits using RSA algorithm. The public key ID 4F0BDACC matchs the last 8 bits of key fingerprint. The key fingerprint is a hash of your public key.
It also lists our user ID information: your name and your email address. And it also indicates the subkey which is 2048 bits using RSA algorithm and the unique identifier of the subkey.
Install Gpg Generated Keys Linux 10
Now you can find that there are two files created under ~/.gnupg/private-keys-v1.d/ directory. These two files are binary files with .key extension.
Export Your Public Key
Others need your public key to send encrypted message to you and only your private key can decrypt it. Use the following command to export your public key. --armor option means that the output is ASCII armored. The default is to create the binary OpenPGP format. user-id is your email address.
The exported public key is written to pubkey.asc file.
Export Your Private Key
Issue the following command to export your private key.
The exported key is written to privkey.asc file.
Protect Your Private Key and Revocation Certificate
Your private key should be kept in a safe place, like an encrypted flash drive. Treat it like your house key. Only you can have it and don’t lose it. And you must remember your passphrase, otherwise you can’t unlock your private key.
You should also protect your revocation certificate. If others have your revocation certificate, they can immediately revoke your public/private keypair and generate a fake public/priavte keypair.
In part 2 we will look at how to encrypt message with your public key and how to decrypt it with your private key. Take care!