Private Key And Public Key Generation
- What Is A Private Key
- Private Key And Public Key Generation Download
- Public And Private Key Examples
- Private Key And Public Key Generation Review
The public key consists of the modulus and the public exponent. A minimal private key would consist of the modulus and the private exponent. There is no computationally feasible surefire way to go from a known modulus and private exponent to the corresponding public exponent. Jul 09, 2019 Public Key Infrastructure (PKI) security is about using two unique keys: the Public Key is encrypted within your SSL Certificate, while the Private Key is generated on your server and kept secret. All the information sent from a browser to a website server is encrypted with the Public Key, and gets decrypted on the server side with the Private Key.
Malware).Using these helps you in two ways:.Malware on PC is reduced to message forgery while the smartcard is insider. The idea is the key never leaves the device under any circumstances because the client can't be trusted (i.e. Lost computer where private key was generated play store.
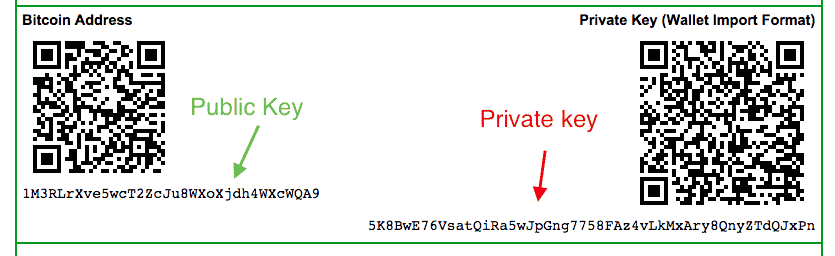
- The Public and Private key pair comprise of two uniquely related cryptographic keys (basically long random numbers). Below is an example of a Public Key: 3048 0241 00C9 18FA CF8D EB2D EFD5 FD37 89B9 E069 EA97 FC20 5E35 F577 EE31 C4FB C6E4 4811 7D86 BC8F BAFA 362F 922B F01B 2F40 C744 2654 C0DD 2881 D673 CA2B 4003 C266 E2CD CB02 0301 0001.
- PuTTYgen is an key generator tool for creating SSH keys for PuTTY. It is analogous to the ssh-keygen tool used in some other SSH implementations. The basic function is to create public and private key pairs. PuTTY stores keys in its own format in.ppk files.
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys, which may be disseminated widely, and private keys,which are known only to the owner. The generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one-way functions. Effective security only requires keeping the private key private; the public key can be openly distributed without compromising security. In such a system, any person can e. The private key is then used to generate the public key using a multiplication on an elliptic curve: The private key (K) will be multiplied by a point generator (G) located on the curve and the result will correspond to the public key (K), another point on the curve (or K = K.g). Open Public Key As the name suggests, the private key is meant for you and only you. Never copy/save this on a server! The public key, however, is meant to be saved on the servers you intend to access, in the “/.ssh/authorizedkeys” file (or rather, pasted/added to this file).
Generate RSA keys with SSH by using PuTTYgen
One effective way of securing SSH access to your cloud server is to usea public-private key pair. This means that a public key is placed onthe server and a private key is placed on your local workstation.Using a key pair makes it impossible for someone to log in by using justa password, as long as you set up SSH to deny password-basedauthentication.
What Is A Private Key
This article provides steps for generating RSA keys by using PuTTYgen onWindows for secure SSH authentication with OpenSSH.
Generate keys
In Windows, use PuTTYgen to generate your public and private keys.
- If needed, download PuTTYgen from the PuTTY download page.(PuTTYgen might have been installed previously with PuTTY or WinSCP.)
- Launch the program, and then click the Generate button.The program generates the keys for you.
- Enter a unique key passphrase in the Key passphrase andConfirm passphrase fields.For additional information about using passphrases,see Log in with a SSH Private Key on Windows.
- Save the public and private keys by clicking the Save public keyand Save private key buttons.
- From the Public key for pasting into OpenSSH authorized_keys filefield at the top of the window, copy all the text (starting with ssh-rsa)to your clipboard by pressing Ctrl-C.You need this key available on your clipboard to paste eitherinto the public key tool in the Control Panel or directly into theauthorized keys on your cloud server.
Use the key pair
Private Key And Public Key Generation Download
You can use the RSA key pair in the following ways.
Public And Private Key Examples
Specify your SSH key when creating a new cloud server
When you create a cloud server, you can assign a public key from the list of keys.If your key is not already in the list, you may add it, and then assign it.
Add a new public key to the list
Private Key And Public Key Generation Review
- Under Advanced Options on the Create Server page, click Manage SSHKeys.
- Select public key for the cloud server from the SSH Keys listand click Add Public Key.
- Enter the key name, select the region, and paste the entire publickey into the Public Key field. Then click Add Public Key.
- Go back to the Create Server page, and confirm that your key is listedin the SSH Key list.
Assign a public key
- Under Advanced Options on the Create Server page, select the publickey you want to use from the SSH key drop-down menu.
- When you are done specifying the all the other details for the server,click Create Server.
Assign your SSH Key to an existing cloud server
To make use of your newly generated RSA key pair, you must tell PuTTY touse it when connecting to your cloud server.
Microsoft office professional plus 2010 free product key generator. It has also enhanced improved picture formatting tools like as color saturation and artistic effects.
To edit the file (or create it), run the following command on the cloud server:
Paste the text onto its own line in the file.
You must have the key available in your clipboard to paste it. The key and itsassociated text (the ssh-rsa identified at the start and the comment at the end)must be on one line in the file. If the text is word-wrapped onto multiple linesan error might occur when connecting.
If you created the authorized_keys file, change its permissionsafter you’re done editing it by running the following command:
Open PuTTY, and go to the SSH > Auth section.
Browse to the location of the key file, and load the private key.
Go to the Session page, and save the session. This saves the configurationso that PuTTY uses the key every time that you connect to your cloudserver.
After you save your session, your key is loaded automatically when youconnect to your server.
Related article
Experience what Rackspace has to offer.
©2020 Rackspace US, Inc.
Except where otherwise noted, content on this site is licensed under a Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License