Certificate Installation Generate Key Nginx Digital Ocean
Last updated: 14/01/2016
- Certificate Installation Generate Key Nginx Digital Ocean City
- Certificate Installation Generate Key Nginx Digital Ocean 2
- Certificate Installation Generate Key Nginx Digital Ocean City
- Digital Ocean Nginx Ssl
This article assumes you've received your certificate from the Certificate Authority, and that you wish to install it on your Nginx webserver. If you want to know how to request a certificate, please consult the « How to generate a certificate request with OpenSSL » article.
- Jun 23, 2015 How To Create an ECC Certificate on Nginx for Debian 7. Create an Elliptic Curve Cryptography (ECC) key pair for more efficient certificate encryption. ECC keys provide security equivalent to that of larger RSA keys while being smaller in size, reducing the resources needed on the server and offering faster performance for mobile devices.
- Jul 21, 2015 Did you install an SSL certificate on your CentOS or Fedora hosted server using Nginx as the Web server? If not, you may want to consider it. With hackers targeting businesses large and small, even Google is nudging site owners to heighten website security.
- Apr 21, 2016.
Nginx - SSL certificate installation
We’ve installed the Let’s Encrypt agent to generate SSL/TLS certificates for a registered domain name. We’ve configured NGINX to use the certificates and set up automatic certificate renewals. With Let’s Encrypt certificates for NGINX and NGINX Plus, you can have a simple, secure website up and running within minutes.
Step 1: Building a certificate bundle
Unlike Apache, Nginx needs all its SSL certificates to be concatenated into one bundle containing the root certificate, the intermediate certificate and your own certificate. The order in which you concatenate the certificates is important:
- The first certificate in the file should be your own server certificate
- Then followed by intermediate certificate, if any - there usually is one, sometimes two
- Then followed by the root certificate
The root certificate is not strictly needed in this list, since browsers have CA's root certificates built-in, however it may be best practice to include it.
Depending on the Certificate Authority you ordered your certificate from, you may receive the certificates either as distinct files, all bundled in one file, or your certificate in one file and all CA certificates in a bundle. Most commonly, you will receive your own certificate as a separate file, and another file containing intermediate and root certificates for use in Apache.
If you have received separate files from the CA, use the following command to concatenate the certificates in reverse order. If there's only one intermediate certificate, you only need to concatenate that one, of course.
If you received your own certificate in a separate file, and the CA certificates in a bundle, execute the following command to create your bundle:
If you received all certificates in a single bundle, just move the file over to your certificate directory, for instance /etc/certs.
Step 2: Edit the Nginx virtual hosts file
Open the SSL virtual hosts file of your Nginx server. Depending on your distribution, it could be found at one of the following locations, or if you installed from source, somewhere entirely different (but then, you probably won't be needing this manual):
- /etc/nginx/conf.d/ssl.conf (Red Hat, CentOs and Fedora Linux)
- /etc/nginx/sites-available/www.mydomain.com (Debian and Ubuntu)
Add a new server block to the virtual hosts file. Note that in the example below, you should modify the paths so that they point to your website's root directory, and the SSL directives so they point to your SSL certificate and your private key. Ms office 2013 key generator free download. It may be easier to copy and modify an existing server entry in your config file.
Please note that the above is only a minimal working server configuration, and that your web server should be tuned for optimum security and performance. You may want to check out our articles on tuning and securing Nginx in the Knowledge Base.
Step 3: Test your configuration
It's good practice to check your server configuration before restarting Nginx. Modify the command below to point to your main Nginx configuration file if it's in a different location.
Step 4: Restart Nginx
Restart Nginx to apply your new configuration:
Step 5: Troubleshooting
If you didn't concatenate your certificates in the correct order, Nginx will fail to start and display an error similar to the following one:
In that case, try to concatenate your certificate files in the correct order again.
If your certificate doesn't display correctly in a browser, check if all certificates are being sent correctly to a browser with the following command, replacing www.kinamo.be with your own domain name:
You should see a chain of certificates starting with your own one, and going up through the different intermediate certificates.
Step 6: Security Test
Visit Qualys SSL Labs' test page to check if your web server and SSL certificate are up to par with modern-day security standards.
Related
Introduction
This article explains how to create an Elliptic Curve Cryptography (ECC) SSL certificate for Nginx. By the end of this tutorial, you will have a faster encryption mechanism for production use.
Traditional public-key cryptography relies on the near-impossibility of factoring large integers. On the other hand, ECC relies on the impossibility of resolving random elliptic curves into discrete logarithmic functions, a problem that’s called the “elliptic curve discrete logarithm problem” or ECDLP. In short, ECC offers smaller keys with similar security, and this in turn translates into higher encryption performance, applicable to digital signatures like SSL.
This tutorial, and all ECC certificates, depends on an elliptic-curve protocol which can come in several flavors. The National Institute of Standards and Technology (NIST) Suite B specifies two potential elliptical curves for use, P-256 and P-384, otherwise known as prime256v1 and secp384r1. For simplicity, we will use the former, prime256v1, as it is simple but practical.
Prerequisites
To follow this tutorial, you will need:
- One fresh Debian 8.1 Droplet
- A sudo non-root user, which you can setup by following steps 2 and 3 of this tutorial
- OpenSSL installed and updated
To test, you will need one of two systems, with OpenSSL installed and updated:
- Another Linux Droplet
- Linux-based local system (Mac, Ubuntu, Debian, etc.)
Step 1 — Install Nginx
In this step, we will use a built-in package installer called apt-get. It simplifies management drastically and facilitates a clean installation.
In the link specified in the prerequisites, you should have updated apt-get and installed the sudo package, as unlike other Linux distributions, Debian 8 does not come with sudo installed.
Camtasia 9.1 key generator. Run as admin the Patch and apply it!4.
Nginx is the aforementioned HTTP server, focused on handling large loads with low memory usage. To install it, run the following:
For information on the differences between Nginx and Apache2, the two most popular open source web servers, see this article.
Step 2 — Create Directory
This section is simply and short. We need to store the private key and certificate in a memorable location, so we need to create a new directory.
Step 3 — Create a Self Signed ECC Certificate
In this section, we will request a new certificate and sign it.
First, generate an ECC private key using OpenSSL’s ecparam tool.
- The
outflag directs output to a file. For this tutorial, we will save the key in/etc/nginx/ssl/nginx.key. - The
nameflag identifies the elliptic curveprime256v1.
Then, generate a certificate signing request.
- The
keyflag specifies the path to our key, generated in the previous command. - The
outflag specifies the path to our generated certificate.
Invoking this command will result in a series of prompts.
- Common Name: Specify your server’s IP address or hostname.
- Challenge Password: Do not supply one.
- Fill out all other fields at your own discretion. Hit
ENTERto accept the defaults.
Finally, self-sign the certificate. The certificate is then used by the client to encrypt data only the server can read.
x509is the OpenSSL tool used to generate the certificate.- The
daysflag specifies how long the certificate should remain valid. With this example, the certificate will last for one year. inspecifies our previously-generated certificate request.
Set the file permissions to protect your private key and certificate. For more information on the three-digit permissions code, see the tutorial on Linux permissions.
Your certificate and the private key that protects it are now ready for setup.
Step 4 — Setup the Certificate
In this section, we will configure Nginx virtual hosts with the key and certificate. In effect, our server will begin serving HTTPS instead of HTTP requests.
Open the server configuration file using nano or your favorite text editor.
At the top of the configuration file, you will find a block of code, akin to the following:
The next few edits will be made inside the server block.
- First, comment out the first two lines of the
serverblock, by preceding the line with a pound sign:
- Then, uncomment the first
listenline underneathSSL Configurationby removing the pound sign. Indent properly, and also removessl default_server.
Update the root directory, directly underneath the commented block. the original reads
server_name _;. Change it to include your server ip, so that it readsserver_name your_server_ip.After
server_name, add your SSL key and certificate paths.
- Finally, add SSL settings.
Your final result should be identical to the following.
Once these changes have been made, save and exit out of the file.
Restart Nginx to apply the changes.
Step 5 — Test Nginx with ECC
Certificate Installation Generate Key Nginx Digital Ocean City
In this section, we will test the server, through the command line. Once again, this may be done on either (1) your local Linux-based system or (2) another Droplet. You may also run this command from the same shell window, but you may want a more solid proof of success.
Open connection via the HTTPS 443 port.
openssl s_client -connect your_server_ip:443
Scroll to the middle of the output after the key output, and you should find the following:
Certificate Installation Generate Key Nginx Digital Ocean 2
Of course, the numbers are variable, but this is success. Congratulations!
Certificate Installation Generate Key Nginx Digital Ocean City
Press CTRL+C to exit.
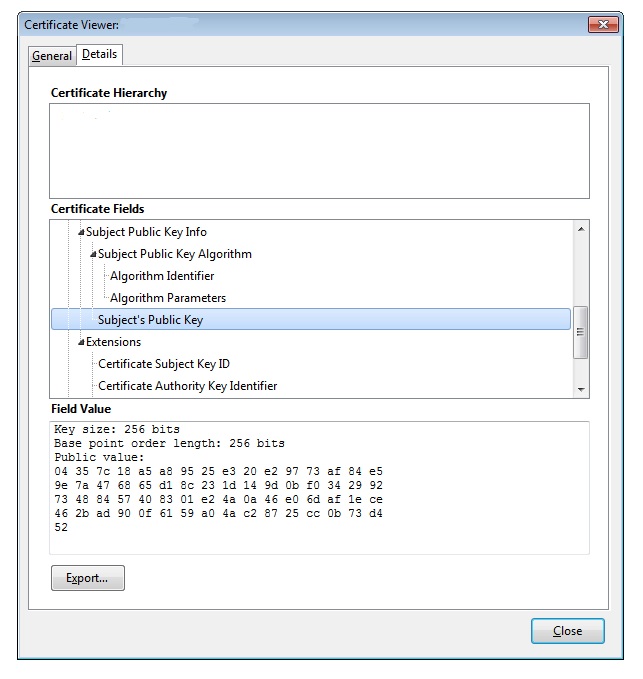
You can also visit your site in a web browser, using HTTPS in the URL (https://example.com). Your browser will warn you that the certificate is self-signed. You should be able to view the certificate and confirm that the details match what you entered in Step 4.
Conclusion
Digital Ocean Nginx Ssl
This concludes our tutorial, leaving you with a working Nginx server, configured securely with an ECC certificate. For more information on working with OpenSSL, see the OpenSSL Essentials article.